Last year, I built a small tool to detect inline styles and scripts in a given webpage/document and then calculate their hashes. It can be useful for someone trying to write a strict “Content-Security-Policy” (CSP) for pre-built websites. I described the reasoning at the time in this blog post.
Today, I’m writing to announce that I released the version 0.0.5 of inlinehashes. The main changes are:
- CSP directives are now displayed for each hash, helping you to know right away where to place them.
- The
--targetoption now uses CSP directives to filter the output instead of needing to remember any custom value. - New output formats were added, instead of relying just on JSON.
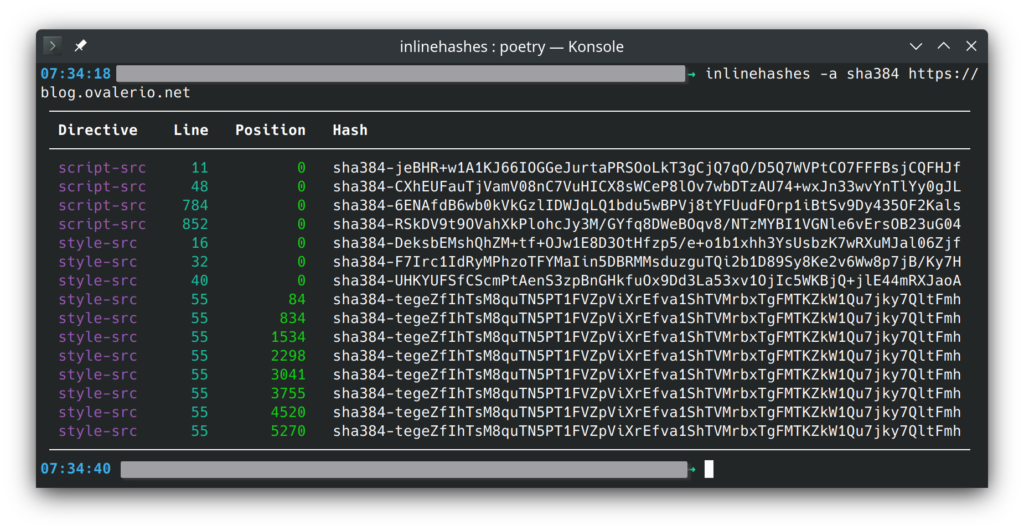
One problem of this version is that it only supports Python 3.11. So for other interpreter versions, you are stuck with version 0.0.4. I expect to fix this soon and make everything work for, at least, the last three versions of Python.
You can find out more on PyPI and on the source code repo.